MiLACNIC Security Module
What is the MiLACNIC security module?
The security module allows users to view information on security events relating to the IP resources of the organizations they manage. The service is offered by LACNIC CSIRT to its members and can be found in the MiLACNIC Reports menu.
The use of this module provides administrators with useful information to identify and correct the different types of security issues that are reported.
Sources of information
The main sources of information used by the security module are the data generated by the projects carried out by LACNIC CSIRT, information received from public sources, and information obtained from commitment indicators shared on platforms commonly used by the CSIRTs community.
Access to the MiLACNIC security module
To view the security module, you must login to the MiLACNIC system with a user with administrator privileges within the organization.[1]
After logging into the system, go to the Reports menu and select Security [Figure 1].
After entering the Security module, users will be presented with a screen [Figure 2] which may or may not display a list of resources, depending on whether events have been detected.
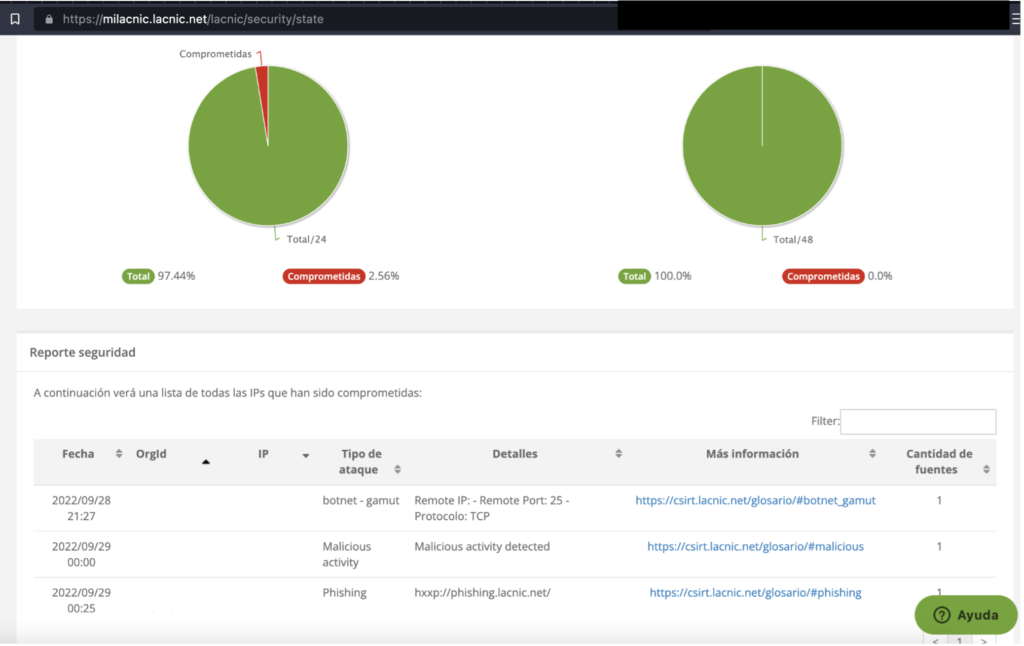
Information available in the security module
The MiLACNIC security module currently shows security events that have occurred and are related to the resources assigned to a given organization. More specifically, it lists the IP addresses involved in botnets, phishing, open resolvers, or those that have interacted with any of the sensors on our sensor network (HoneyNet).
While less frequently, it also alerts about IP addresses that are exposing a service that may be used by attackers to launch denial-of-service attacks against third parties. These services can be open resolvers or some other protocol that allows amplification attacks like those described in the Study of Internet Resources in the LACNIC Service Region that Use UDP and Enable DDoS Attacks.
It should be noted that the IP addresses listed under Malicious activity are resources which our sensor network observed as having performed some type of suspicious activity. Bearing in mind that our sensors are designed to simulate a vulnerable system, any activity carried out in these sensors is considered suspicious or malicious.
Why is it important to monitor security reports?
If one or several IP addresses are listed in the security module as having some type of malicious activity:
- A user of a system behind that IP address may have been performing the activity directly.
- A system behind that IP address may have been compromised and is being used by an attacker for malicious purposes.
- A system that allows redirecting network traffic may be being used to anonymize attacks (e.g., an open proxy).
- If resources involved in a botnet have been detected, the infected systems are being controlled by a malicious actor and may be used to carry out various cybercrimes.
- If an open resolver has been detected, this means that this DNS accepts queries originating anywhere on the Internet. Someone may use it to launch a denial-of-service attack against third parties.
Recommendation
LACNIC CSIRT recommends checking this module at least once a week, analyzing the types of security events and implementing measures to correct these vulnerabilities.
LACNIC HoneyNet Project
Open Resolvers Project:
- https://csirt.lacnic.net/dns-open-resolvers-con-ipv4
- https://csirt.lacnic.net/dns-open-resolvers-con-ipv6
Study of Internet Resources in the LACNIC Service Region that Use UDP and Enable DDoS Attacks:
Authors: Graciela Martinez, Guillermo Pereyra
[1] Plans are in place to extend this feature to all MiLACNIC user profiles.
